Your Stolen Data’s Price Tag: What Hackers Will Pay for Your Personal Information
The internet is vast and multi-layered, and deep within it, a shadowy marketplace thrives, hidden and unseen by most, but known by everyone, as the Dark Web. This secretive network is a thriving marketplace where cybercriminals buy and sell stolen data and possibly even your personal information, and there is little anyone can do to stop them.
Understanding how hackers steal and sell this information is important for anyone looking to protect themselves in the digital age, especially now with the rise of AI making those talented in these skills even more proficient.
Cybercriminals use a variety of methods to steal personal information. Deepfakes, Phishing, Vishing, Whaling and Smishing being some of the most common tactics, and often involve tricking individuals into providing sensitive data by pretending to be a trustworthy entity. Phishing emails and fake websites designed to look like legitimate ones, can deceive even the most cautious of people. Another method is through data breaches, where cybercriminals exploit vulnerabilities in systems to access vast amounts of data stored by organizations. Once inside, they can extract everything from credit card numbers to private government information such as birth dates and social security info.
Malware, malicious software designed to infiltrate computers, also plays a significant role and websites, and even our very emails, contain Viruses, Worms and Trojan Horses as well as Spyware, Ransomware Adware and Rootkits (if you don’t know what some of these are, maybe it is time to start learning!) These malicious programs can record keystrokes, capture screenshots, and send this information back to the hackers.
Once hackers obtain this information, it is packaged and sold on the Dark Web. This hidden part of the internet, accessible only through special software like Tor, provides anonymity to both buyers and sellers, making it an ideal platform for illegal activities. The Dark Web is not just a haven for stolen data; it also hosts a variety of illicit goods and services, creating a thriving underground economy.
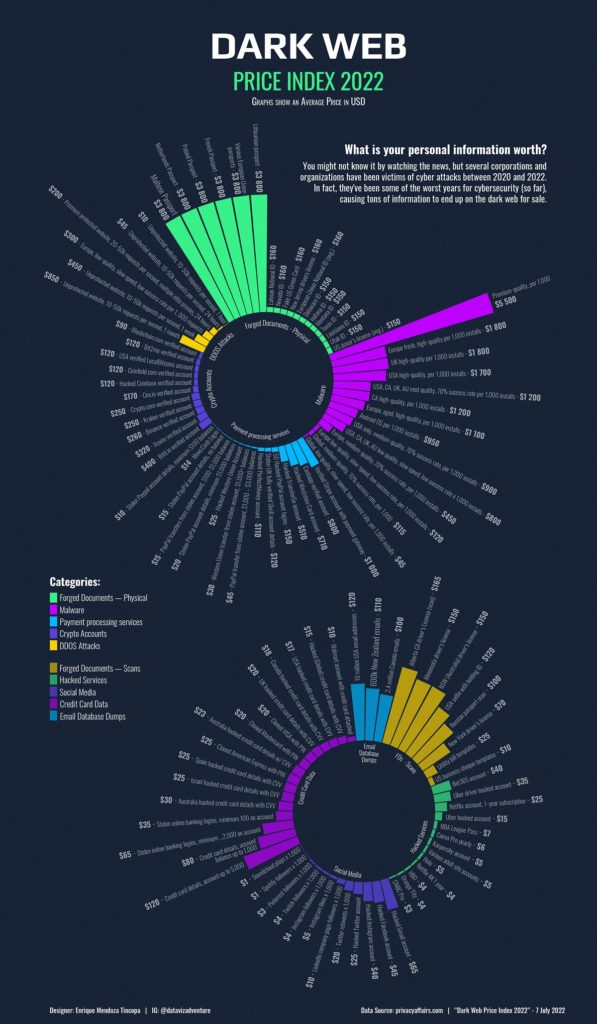
The Value of Stolen Data
Hackers operate information rings with stolen data by selling it to the highest bidder. The Dark Web Price Index 2023 (According to Express VPN) provides a detailed look at the going rates for various types of personal data. Credit card information, for instance, is a hot commodity. U.S., EU, and Australian credit cards typically sell for $20-$30, while Asia-based credit cards fetch around $39.90.
Crypto account logins are also highly valuable, with prices reflecting the potential for high rewards. Logins for Crypto.com can sell for $300, while Binance and Gemini accounts are priced at $200 and $349 respectively. E-commerce logins with saved payment information are another lucrative target, with Amazon and eBay accounts selling for $25 and $120, respectively.
Social media logins are less expensive but still valuable. Facebook accounts can sell for $45, while Instagram and TikTok logins are priced at $40 and $25, respectively. Streaming and gaming logins, such as Netflix and Hulu, go for around $9.99, highlighting the diverse range of data that can be sold.
What Hackers Do with Stolen Data
Hackers and buyers of stolen data use this information in various ways. One common use is identity theft. With enough personal information, a cybercriminal can open new credit accounts, take out loans, or even file fraudulent tax returns in the victim’s name. This can lead to devastating financial and personal repercussions for the victims.
Another use is in creating synthetic identities. This involves combining real and fake information to create a new identity that can be used to commit fraud. Synthetic identities are harder to detect and can be used to obtain credit, commit tax fraud, or carry out other illegal activities.
Stolen data is also used for targeted phishing attacks. With detailed personal information, hackers can craft convincing phishing emails using AI that appear to come from legitimate sources, increasing the likelihood that the recipient will fall for the scam. Now with the advent of Deepfakes, hackers can even impersonate an entire board of directors, or just the responsible few who need to authorise an online transaction, bypassing protocols and emptying accounts in seconds.
Who Buys Stolen Information?
People who buy stolen information are as varied as the methods used to steal it. Some are individual criminals looking to make a quick profit, while others are part of organized crime syndicates that use your info for large-scale fraud operations. There are also middlemen who buy data to resell it at a higher price.
Businesses can also be buyers, this is highly illegal, and some of them are looking for that competitive edge to take out or even sabotage rivals. Governments even employ people to purchase data for spying on individuals or organizations of interest to gather sensitive information or to leverage them into acting in a specific way at a pre-ordained time.
Protecting Yourself from Data Theft
Given the rise in demand for stolen data, it is crucial for us to take steps to protect our personal information. One of the first things you can do is use strong, unique passwords for each of your online accounts and consider using a password manager to keep track of them.
Enabling two-factor authentication (2FA) wherever possible adds an additional layer of security, making it harder for hackers to access your accounts even if they have your password.
Be cautious about the information you share online, especially on social media. Personal details like your birthday, address, or phone number can be used to steal your identity. Be skeptical of random emails or messages asking for personal information, and always verify the sender’s identity before responding or clicking on any links that are provided.
Staying Informed and Vigilant
Staying informed about the latest cyber threats and security best practices is essential. Follow reputable sources for cybersecurity news and updates. Many organizations like Cyberdexterity offer free resources and articles to help individuals understand the risks and protect themselves.
The value of your personal information on the Dark Web highlights the importance of cybersecurity awareness and being proactive in protecting your data, and by taking steps to secure your digital presence online, you can reduce the risk of falling victim to cybercrime.
Stay vigilant, stay informed, improve your Cyber Dexterity and develop a “Sixth Sense” when it comes to Malware and ‘the hooks” used when attempts are made to steal your information.
AI is becoming more aware, are you?
For more on improving your Digital Dexterity have a look at this article:
Do you have the right level of Digital Dexterity? – CyberDexterity